Table of Contents
Introduction
How To Use SFTP – As technology advances, data transfer has become more popular, and the mobility of information is critical for collecting insights from your customers. This file transfer is frequently insecure, and the problem must be handled immediately.
In today’s data-driven society, transferring a file with the highest level of security is critical. If the file ends up in the wrong hands, a simple oversight could result in a security breach and a slew of negative implications for the firm. There are a variety of ways to secure this process, but in this post, you’ll discover how to use SFTP (Secure File Transfer Protocol) to transfer your data.
What is SFTP?
SFTP (Secure File Transfer Protocol) is a file protocol that allows file transfers securely between computers or over the internet. This application is based on FTP, and it includes SSH (Secure Shell) security features.
SFTP transmits files using SSH and FTP, a cryptographic component of internet security. In order to prevent middle-man attacks, a server must authenticate the client.
When sensitive information needs to be transferred securely over the internet or between computers, SFTP is employed. Trade data, for example, may not be protected by any data privacy laws, but it can be disastrous if it falls into the wrong hands. As a result, a company may desire to use SFTP to send files securely.
How does SFTP works?
SFTP (SSH File Transfer Protocol or Secure File Transfer Protocol) is a more secure choice than FTP for securing server-to-server file transfers between yourself, your trading partners, and enterprise servers.
Secure File Transfer Protocol (SFTP) establishes a secure connection and provides companies with a greater level of file transfer security by using the Secure Shell (SSH) data stream. This is because SFTP uses encryption techniques to send data securely to your server while keeping files unreadable, and authentication prevents unauthorized file access during the process.
While SFTP doesn’t require two-factor authentication, you may make it more secure by requiring both a user ID and password, as well as SSH keys. Imposters cannot connect to the SFTP server if SSH keys are created. SSH key pairs must be created ahead of time.
You can utilize Secure File Transfer Protocol (SFTP) to execute a range of activities on sensitive files, such as deleting files and resuming interrupted transfers. Unlike FTP over SSL/TLS (FTPS), SFTP requires only one port number (port 22) to connect to a server.
Is SFTP safe?
Yes, SFTP encrypts everything sent via the SSH data stream, from user authentication to file transfers; if any part of the data is intercepted, it will be illegible due to the encryption.
There are numerous measures you may take to improve the security of your SFTP servers in order to meet security requirements:
- FTP should be disabled. Disabling FTP on your own server is an excellent method to eliminate a potential attack vector. Similarly, if you engage with a third-party vendor, you might inquire as to whether FTP has been disabled and, if not, what security mechanisms are in place to secure it.
- Use the most secure encryption possible. The strongest standard encryption is now AES-256, while the strongest hash encryption to authenticate data is currently SHA-2 hashing. It’s simple to find an SFTP server that supports both.
- For external access, use file and folder security. When other parties need to see data during or before an SFTP transfer, have adequate procedures in place to monitor and protect it. This contains features like proper user access and identity management.
- For internal access, use folder security. Because access controls must be set up individually on each folders, they can be a nuisance to implement. Because most business users lack the necessary expertise or permissions, organizations frequently rely on these users to submit help desk tickets to IT for access management duties.
- External users should be required to use certificate-based authentication. This manner, you can make sure that everybody who logs into your system has a security certificate that verifies their identity.
- Make your SFTP server more secure. Alternatively, use a provider that uses hardened servers.
- Protect the SFTP server behind your company firewall, and only allow illegal access to a proxy tier across your firewall as a DMZ.
- Include auditing and documentation. Most frameworks necessitate some level of documentation capability for things like compliance and file access. A major aspect of GDPR compliance is having a system in place to track file access and document things like user consent and other requests.
- IP blacklisting and whitelisting are useful tools. To protect data, it may be necessary to simply prohibit access to your servers using blacklists, especially if there is no reason to permit traffic from certain countries or areas.
Prerequisites:
- Make sure you have a steady internet
- If you are using other LINUX systems, your credentials from there (IP, username and password)
- Latest version of Bitvise is installed and ready to use.
Get SFTP Credentials
If your using some other LINUX system, do get your SMTP credentials from there. If your using CloudPages, Follow the below-mentioned steps to get your SMTP credentials.
Go to your Cloudpages project->server. Note your server’s IP and click on your site
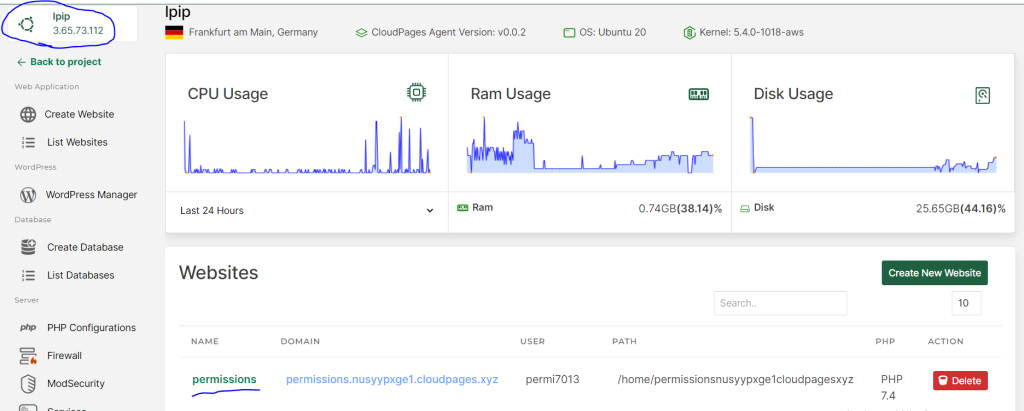
Click on Settings
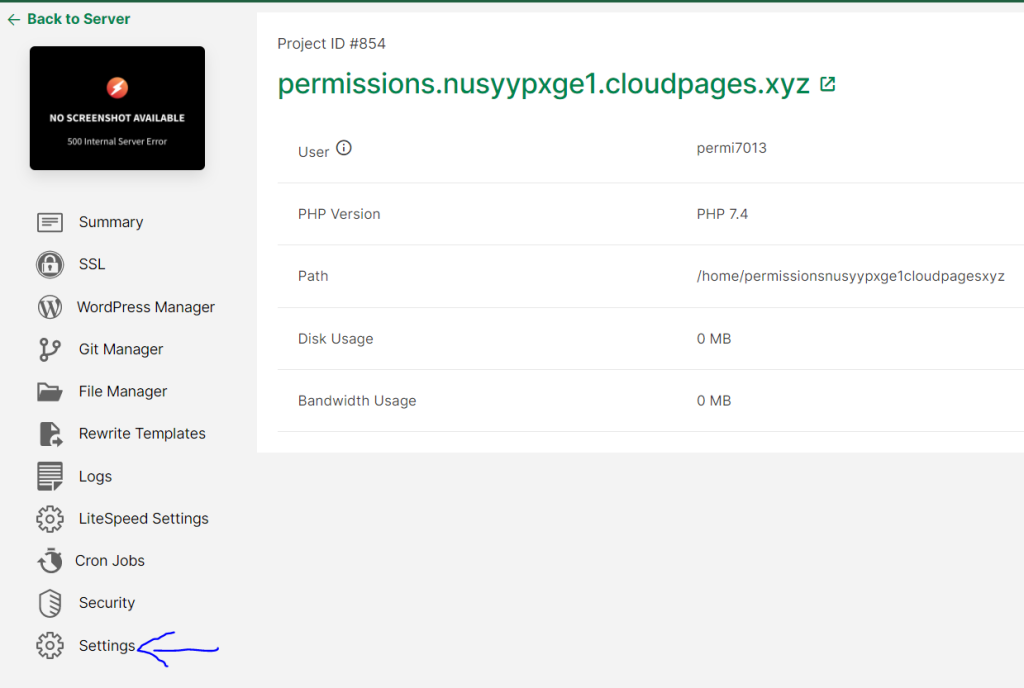
Note your username and click on “Change Password”
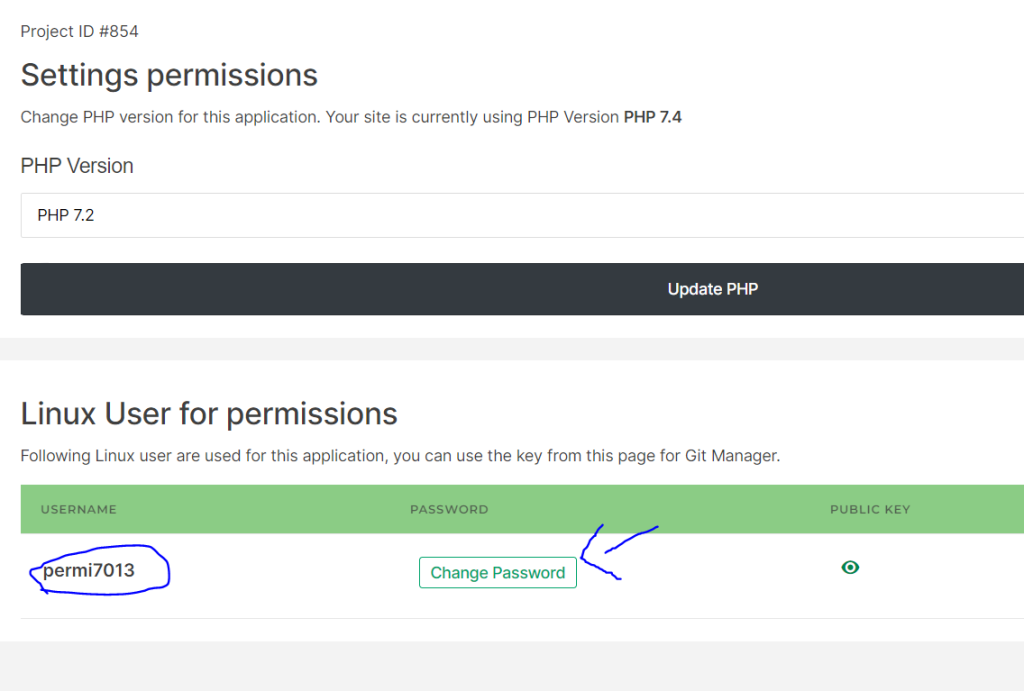
Enter your new password and make sure you note it down. click “Change password”
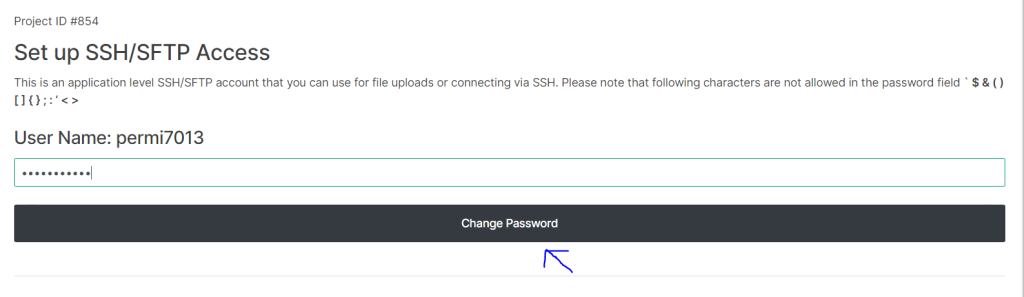
Enter Host (IP), Port = 22, Username and password in Bitvise and login
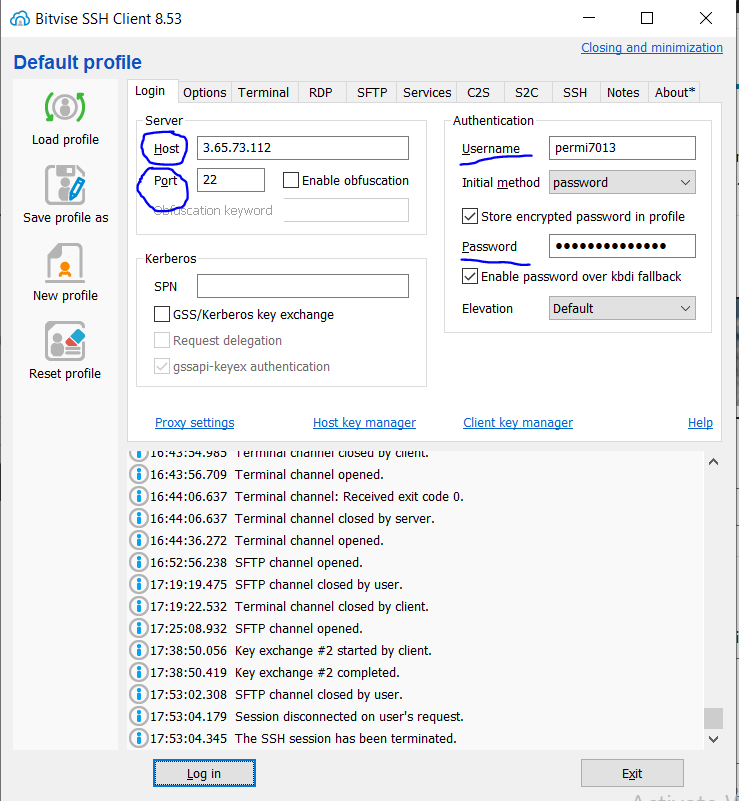
Transfer Files Using SFTP
Using Command console for SFTP file transfer:
First we need to establish an SFTP session by issuing the following command:
sftp user@server_IP
and enter your password
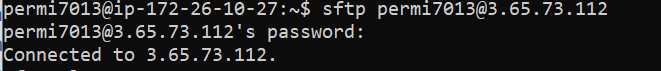
Your prompt will change to an SFTP prompt once you connect to the remote system.
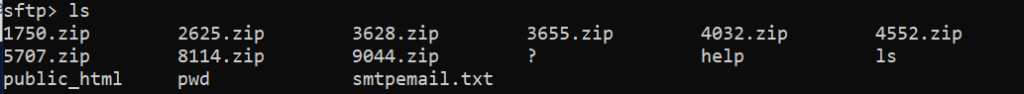
Another well-known command for viewing the contents of the remote system’s current directory is:
sftp> ls
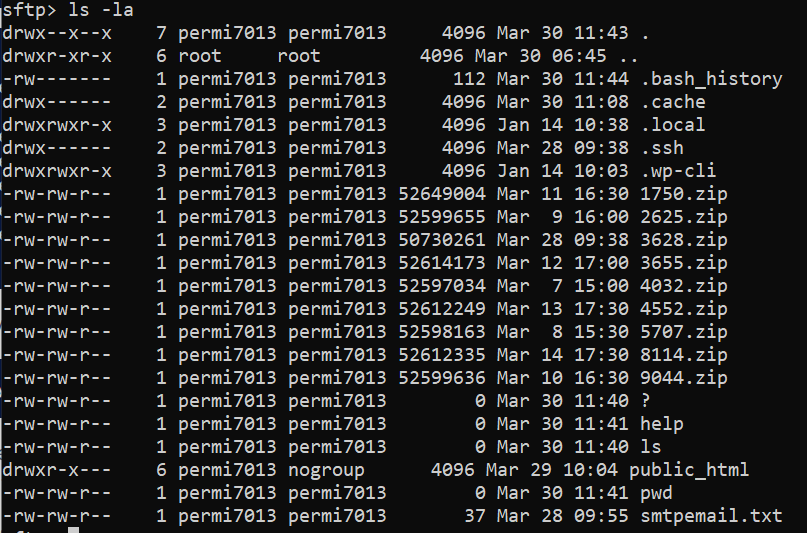
You can add -la to ls to view more file metadata and permissions:
Download files from our remote host
You can use the get command to get files from your remote host:
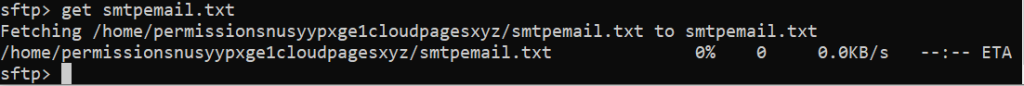
Transferring files to the remote system
The same procedure applies for transferring files to the remote system, but with the addition of a put command:
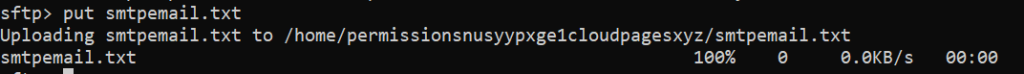
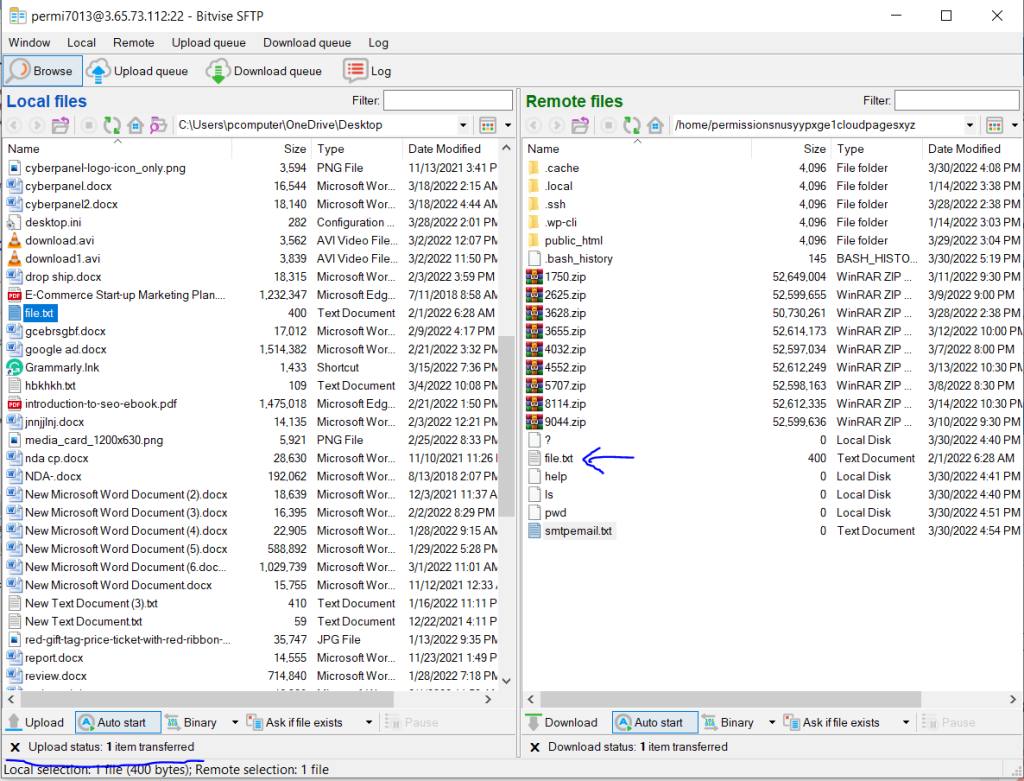
Using GUI:
login to Bitvise SSH Client and click on “New SFTP Window”
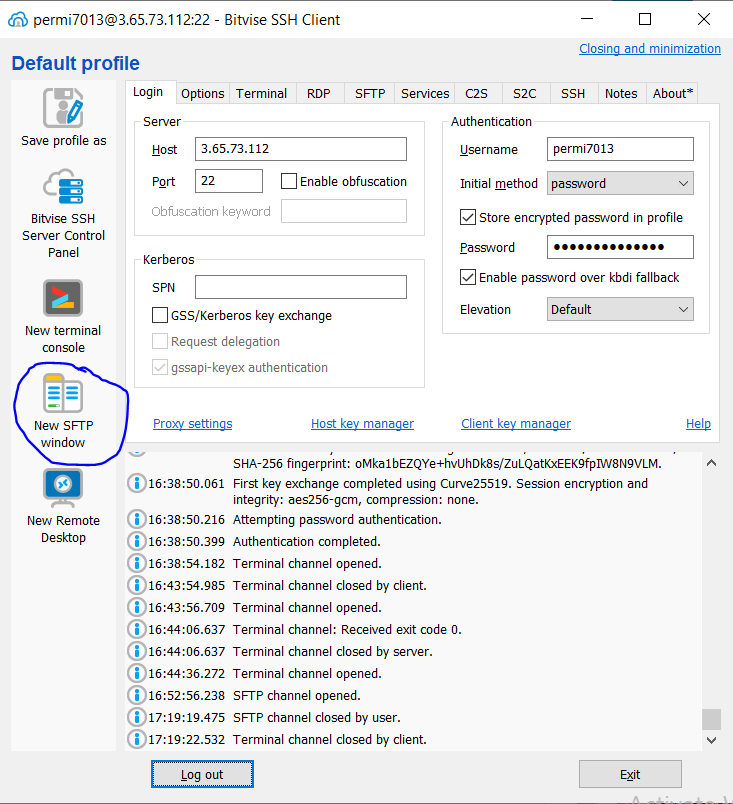
on left side, these are your local file and remote files are on the right.
Now to download file from you remote files simply drag your file from the right side and drop it in the left side (local files side)
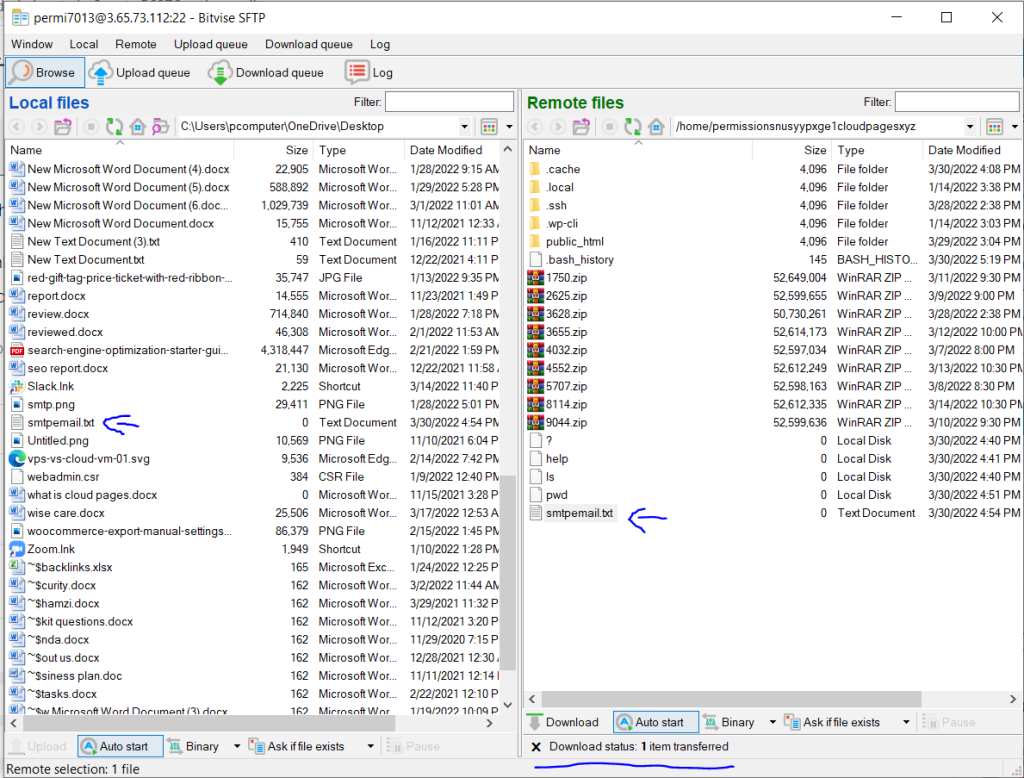
Transferring Local Files to the Remote System
Now to transfer file from your local files simply drag your file from the left side and drop it in the right side (remote files side)
Conclusion
With the advancement of technology, data transfer has become more popular, and information mobility is crucial for collecting insights from your customers. Frequently, this type of file transfer is insecure, and this needs to be fixed right away.
In spite of the less comprehensive features of SFTP syntax, it can be useful for preserving legacy FTP compatibility and for restricting what functionality can be accessed by remote users in some environments.



